Do you have a need to control computer access by users or children to prevent access to certain websites, or at particular times of the day or night? Would you like to monitor websites accessed by them, or those that were blocked? Do you want to protect children from exposure to unknown danger sites? If this sounds like what you need, then this tutorial should help you.
Please note that this tutorial is NOT a software review, but simply a guide to assist you in obtaining, installing, and setting up, and use of K9 Web Protection. K9 Web Protection is free for home use only, and a license fee is payable for use in any business. K9 Web Protection works on Windows 32 and 64 bit versions from XP onwards as well as MacOSX 10.4.11 and later. Versions are also available for IPhone, IPad, IPod, and Android devices.
Downloading & Installing K9 Web Protection
K9 Web Protectioncan be downloaded HERE only after you supply a legitimate email address. After submitting a download request, you will receive an email containing a download link, and your license number. Click the download link and you can save the small installation file to a location of your choice. Locate your install file and double click it to start the installation, during which you’ll be asked to enter the license number you received in the email, and very importantly, create and enter a password to allow access to the program configuration. A reboot is necessary to complete the installation. Should your firewall ask permission to allow K9 Web Protection to communicate with the internet, then of course you should allow it.
K9 Web Protection comes pre-configured, and will startup with your computer with options to suit most uses, but for sure you’ll want to have a look around and become a little familiar with it, maybe customize it. So go to your start menu, click “Blue Coat K9 Web Protection” and on its sub menu “Blue Coat K9 Web Protection Admin”
You should see a dialogue box open in your browser, like the one below, which is from a Windows 7 PC but yours should be similar. This is the home page of the application.
To access “View internet Activity” or “Setup” you’ll need to enter your password you created when you installed the program, so lets click “Setup” and you’ll then be able to enter your password to get into the nitty gritty bits.
The first page of setup of K9 Web Protection is “Web Categories to Block” section which is displayed in Pic: 3 below.
The various “strengths” of blocking filters are listed from “high” down to “minimal”. Selecting these will show slightly different filters so go ahead and have a look if another strength filter suits you. There’s also one marked “Monitor” which allows no sites to be blocked BUT retains a log of sites accessed for future research. The very bottom one “Custom” is worth a look because here you can create a truly one off filter for a special purpose, shown below in Pic: 4 of K9 Web Protection .
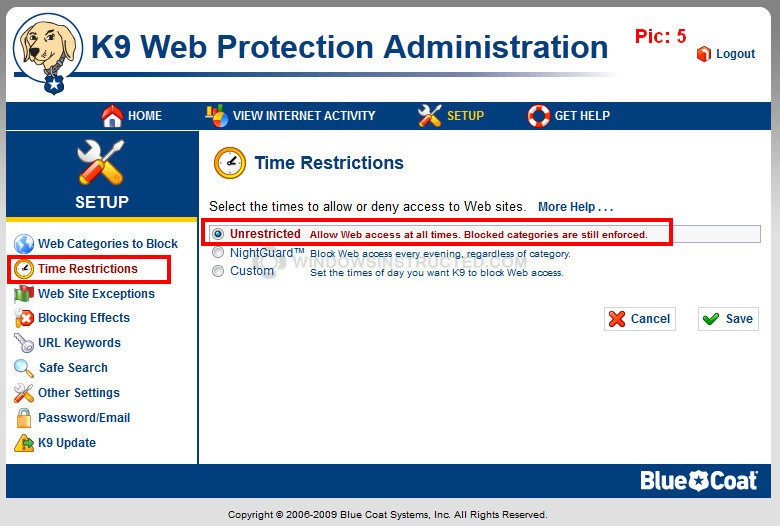
Next item in the left hand menu is “Time Restrictions” and there are three categories of these as shown in Pic: 5 of K9 Web Protection. below.
“Unrestricted” is the default choice here, but should you wish to prevent any internet access during certain hours, then “Nightguard” will allow you to select whatever hours of the DAY or NIGHT that there will be NO internet access. Note that this will occur on a daily cycle.
Perhaps if a daily cycle doesn’t suit or you need to block the net at certain hours on different days, have a look at the “Custom” option, as shown in pic: 6 below. Here you can customize to your hearts content, and really control internet hours. In the example below no internet access will be available between 6:30 to 10:0 PM Monday through Friday. Of course you could choose any thirty minute block (s) wherever.
The next setup option we’ll look at is “Web Site Exceptions” which is quite straightforward. Here you can manually add an internet address to either block, or allow it. The “Blacklist Without Password” option allows a user to block a site, but remember it cannot then be unblocked without using a password. See Pic: 7 below.
The next set of options are “Blocking Effects” which should need no special explanations, and the only non default option chosen as shown in the Pic: 8 below is the “Bark When Blocked” option which simply makes the K9 (canine) dog to bark whenever access to a blocked website is attempted. This could be a handy option for a parent to hear, assuming the computer audio is on that is?
“URL Keywords” is next on the menu list, and here we can insert any keyword, which when saved will prevent any search with that keyword in it, or any link to a website containing that keyword. As an example if we were to insert the word “Queen” into the dialogue box, and save it, then any search with the word “Queen” would be blocked. Pic: 9 below displays this option.
Further down the options list “Safe Search” allows changes to search security, via different search engines. It should not normally be required to change the default options shown below in Pic: 10.
The “Other Settings” options should not require any changes from the default settings, including the “Update to Beta” box which should not be checked. This option is intended for advanced users with a Beta version being possibly less stable than a normal release version of the software. The default settings are shown in Pic: 11 below.
The final two options “Password/Email” and “K9 Update” do exactly that, and should be used when changes to your contact details occur, or you wish to change your password. You can also check for a new program version.
Let’s now look at the logging features of this software, which is accessible by clicking “View Internet Activity” on the menu bar. The activity summary is shown in Pic: 12 below.
There are two options in the left hand panel for this page, “View Activity Summary” and “View Activity Detail”. When “View Activity Detail” is selected the entire details of all categories are displayed which may be overwhelming for new users, so we will concentrate on the “View Activity Summary” page.
As in our example the “Category Hit Summary” lists the different types of searches in three colors.
Green indicates searches acceptable, and successful, for the chosen filter options.
Orange indicates a search category that contains searches that may have been redirected to acceptable web sites, or contains a search term that MAY lead to suspect content.
Red indicates searches that have been refused.
Clicking on any colored category will open a “Detailed Activity View” for that category. See Pic: 13 below for an example, where we clicked on “Adult / Mature Content”.
“General Hit Summary” shown in Pic: 12, lists all searches since the log was last cleared. Again clicking on on any underlined category will show a detailed view of that category. As an example, Pic: 14 below shows a detailed view of “Blocked By Keyword” we referred to in the “URL Keywords” options earlier.
“Recent Admin Events” Pic: 12, shows any changes made to the program configuration, and we can see where “Queen” was added as a “URL Keyword”.
With little experience this software should provide reliable family protection, and with its many options, satisfy the more advanced user.